토요일, 03 4 2021, 06:30 UTC — 일요일, 04 4 2021, 18:30 UTC

[Forensics]

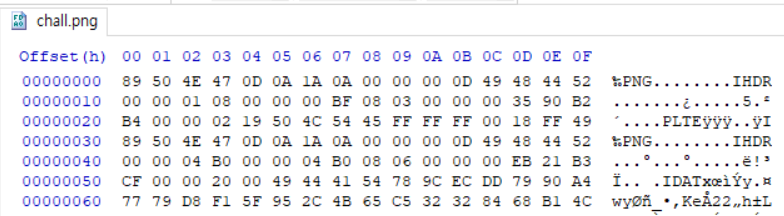
If you look at HxD, you can see that there are two header signatures.
So, I was delete one header signature.

Flag : shaktictf{Y0U_4R3_aM4z1nG!!!!}


There are several packets with a 'pastebin address'.
One of them are real flag.
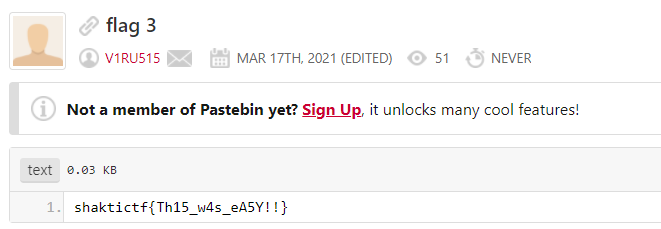
Flag : shaktictf{Th15_w4s_eA5Y!!}


strings network2.pcapng
I got some numbers.

Change decimal numbers to ASCII characters.

Then change the ascii text to base64.
.... I got fake flag.. 'n0tth4tea5y'
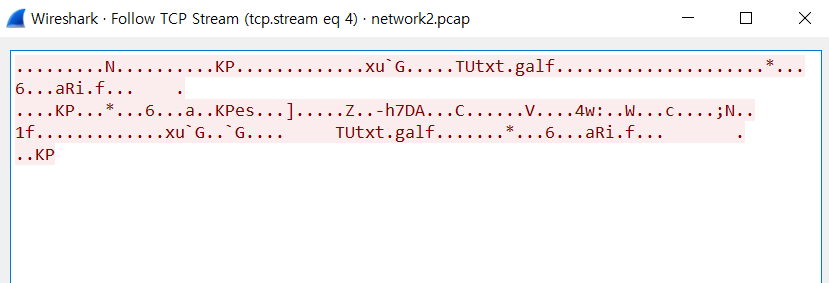
I can see many website address packet in wireshark.
One of them is strange. 'TUtxt.galf'
reversereverse this text.
flag.txt!!

change the ascii to raw and reverse.
f=open("reverse hex.txt")
data=f.read().split(' ')
print(' '.join(reversed(data)))
flag.zip file save.
The file has a password.
The password is fake flag!!!
pw : n0tth4tea5y
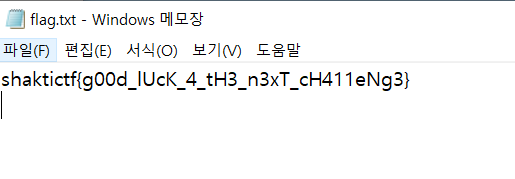
Flag : shaktictf{g00d_lUcK_4_tH3_n3xT_cH411eNg3}

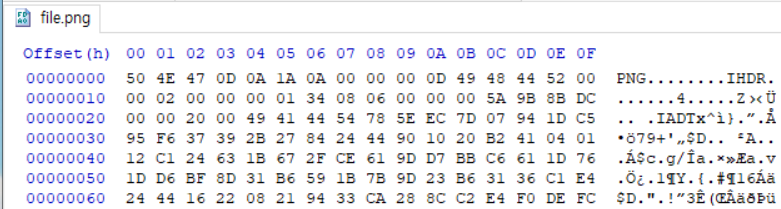
The file has wrong header signature and IDAT chunks.

png header signature : 89 50 4E 47 0D 0A 1A 0A
IDAT : 49 44 41 54

Flag : shaktictf{Y4YyyyY_y0u_g0t_1T}


Check cmdscan among the Volatility options, there is base64 strings.

I got part 1 flag.
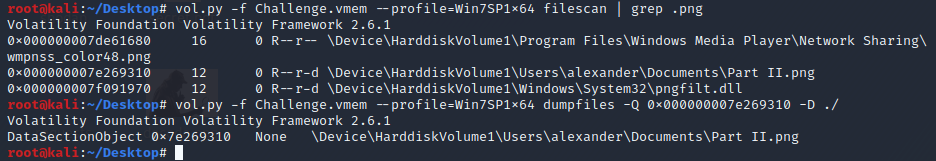
filescan | grep Part
I found Part 2.png file.
dumpfiles Part 2.png
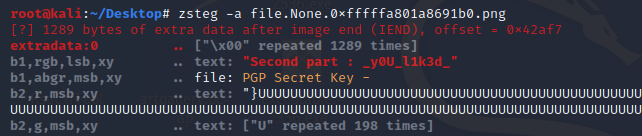
zsteg -a part2.png
so I got part2 flag.
'#CTF 2021' 카테고리의 다른 글
| UMDCTF 2021 write up (0) | 2021.04.19 |
|---|---|
| RITSEC CTF 2021 Write up (0) | 2021.04.11 |
| Tenable CTF 2021 write up (0) | 2021.02.23 |
| SecureBug CTF 2021 write up (0) | 2021.02.19 |
| TrollCAT CTF 2021 write up(2) (0) | 2021.02.07 |



